Hi guys this is Aditya, sorry i wasn't able to update my blog because of exams but anyways I'm back now. So here's my new post.
In this post I'll guide you how to recover your deleted data from your Android device storage or sd card. So how does it fell when you accidentally delete your important data and you want it badly. So here the tutorial for how to recover deleted data from your storage using an Android device.
Requirements
You need root access to use this app. if your device isn't rooted you can check out my other tutorial on How to Root any Android Device
Steps
1. First of all you need to download the an app called Disk Digger it's available on Play Store for free. There is also a pro version version of this app on Play Store which is an paid app.
2. After installing the app. You need to open it and grant root permission
3. Now select the storage from which you want to recover the deleted data.
4. Now a Pop Up will appear asking you to choose the file format you want to recover. Example : If you have deleted a video file then select the .mp4 format.
5. Now click on "OK"
6. As soon as you click OK scanning would start and it would show you all the deleted video files with .mp4 format.
7. Now select the file you want to recover and click on the floppy disk icon.
8. Now a menu would've appear with three options
9. Now select "Save files locally" to recover those files and to save it into your local storage.
That's It now you know how to recover your Deleted data on Android. Thank you keep visiting
How to Recover your Deleted Data on Android
Problems using your smartphone camera.
So today I am going to introduce a new application which can easily
solve mathematical problems using your phone camera, imagine how much
simpler our life would have become in our school days if we had a
gadget that automatically solves mathematic problems and can give us
instant results and solutions to all sorts of mathematical problems.
So this post is for all who are spending times solving hard
mathematical problems.
The name of the App which we will use is Photomath you can download
it from Google Playstore
Benefits of using PhotoMath
* PhotoMath supports basic arithmetic, fractions, decimal numbers,
linear equations and several functions like logarithms. Support for
new Math is constantly added in new releases as the aim is to make all
the Math easy to learn
* Students can use it as a tool to learn Math while parents can use it
to quickly check their kid's homework. With PhotoMath, you can have a
Math teacher in your pocket!
* PhotoMath Gives a step-by-step solution for each and every
mathematical question
Steps to Use Photo Math
1. You need to Go to google play store and search for the app
PhotoMath. You need to install the app on your smartphone in order to
solve maths using your phone Camera.
2. Once you installed the app you will be given a free tutorial on how
to use PhotoMath for solving a problem.
3. After following every tutorial, you will be redirected toward the
main page of the app and you will see a camera over there
4. You need to scan your mathematical question with the help of camera
just like you scan aQR code. Now wait for few second and it will
automatically detect the question and instantly give you the answer
In case if PhotoMath is not able to find the solution to your
mathematics problem this app gives you the option to send a feedback
with the question. Their help team will come in rescue. PhotoMath
works best on printed problem sometimes the camera failed to detect
the problems of handwritten text due to low resolution.
How to Solve Mathematical Problems Using Phone Camera
lost or stolen Android Phone. So, here is an article to teach you how
to track your lost or stolen Android Phone.
Android Device Manager from Google. This is a nice and simple web app
provided by google, where you can track, lock, ring or wipe your phone
remotely. To make this work, you need to have the device registered
with Google ( this is usually done automatically when you sign into
your Google account from your Android phone ) and to allow remote
tracking and control – these options are turned on by default, but you
might have disabled them after you read some privacy related article.
How to Enable Android Device Manager
Requirements :
To make sure that you Android Device Manager can track your phone, you
need to be signed in with a google account. An account that you can
use from your desktop too ( not one that you create specifically for
your smartphone and don't remember the password ).
Steps
1. Android Device Manager and remote tracking can be turned on and off
from your phone settings. In your main Settings app tap on Google,
then tap Security. You have to enable "Remotely locate this device"
and "Allow remote lock and erase"
2. To track the phone, you have to be sure that Location is turned on.
In Settings app, go to Location, and tap to turn on the location
tracking.
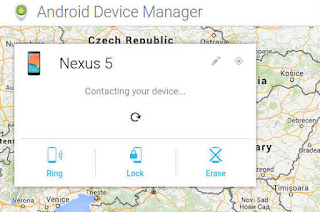
3. To check if everything is set-up correctly, go to Android Device
Manager and see it in action. As you can see, it will automatically
find your phone location ( if it is available ), and will give you
options to Lock it, Ring for 5 minutes, or Wipe it ( erase ). To work,
Internet access should be present and location settings activated.
Link to Android Device Manager : goo.gl/6mg1QM
How to Track your Lost or Stolen Android Phone
security researchers and pentesters. It offers advanced penetration
testing tool and its ease of use means that it should be a part of
every security professional's toolbox.
Now a days more and more apps are available on Android operating
system for smartphones and tablets so it becomes worthwhile to have
Kali Linux on your smartphoneas well.
Requirements.
* Rooted Phone
* Good Internet Connection
* More than 80% charge
Steps
1. Download Linux Deploy App in Your Android Mobile from Google Play Store.
2. Install and open Linux Deploy App in your mobile and click on download Icon.
3. Change the Distribution of Your Linux to Kali Linux.
4. Go to Top of the screen and hit the Install button. This will take
about 5 minutes provided you have a good Internet connection.
5. Download Android VNC Viewer App from Google Play Store.
6. After installing, enter settings given in the screenshot in your
VNC Android App.
7. Click the Connect Button in VNC Viewer App.
Done ! Now you will be able to run Kali Linux on your Android Phone.
How to Install Kali Linux on your Android Phone
you can watch it later. In this article you will learn to download any
youtube video without the use of any software or without copying and
pasting video link.
How to download any Youtube video
Steps
1. Open Youtube website
2. Browse for the video which you wanted to download
3. Now open the video page and click on the URL tab.
4. After clicking the url tab you will se something like this "www.youtube.com"
5. Remove everything before youtube.com and replace it with 9x
Ex: "www.youtube.com"
remove "www." And replace it with 9x like this - 9xyoutube.com
6. Now you you will be taken to another page where you can select
what resolution and format you want to download.
7.Now click the download button and your download will start.
That's it you have downloaded a youtube video.
Easiest Way To Download Youtube Videos
1.) TEKKEN 6
2.) GHOST RIDER
3.) DRAGON BALL Z – SHIN BUDOKAI 2
4.) GOD OF WAR- GHOST OF SPARTA
5.) CRISIS CORE FINAL FANTASY VII
6.) SPIDER MAN 3
7.) TOM CLANCY'S SPLINTER CELL
8.) DISSIDIA 012 FINAL FANTASY
9.) PRINCE OF PERSIA REVELATIONS
10.) BLEACH HEAT THE SOUL 4
Top 10 PPSSPP Games You Must Play
them capable of running graphics-intensive games. However, that
doesn't mean we should leave all the classics behind. There was a time
when PSP( PlayStation Portable) was a big thing, but it got outshined
by today's Smartphones with solid specs.
Fortunately, we don't have to say goodbye to our favorite PSP games as
we can also run them on Android phones. Using a dedicated emulator,
you can easily run almost all types of PSP games on your Android
phone, and in this tutorial, we are exactly going to show you how.
Steps :
1. Open the Google Play Store.
2. Search for "ppsspp" in the Store.
3. Select the "PPSSPP" option.
4. Tap "Install" to download and install the emulator.
5. Download ISO or CSO game files from various sources online.(Also
known as ROM for ppsspp)
6. Launch PPSSPP.
7. Now navigate to the destination on your device memory from ppsspp
where you stored the .iso or .cso file and tap on it.
8. Now go to the games tab and tap on the icon of the game to start playing.
Now you can enjoy your PSP on Android
How to Run PSP Games on Android
the legendary first-person shooter mod for Half-Life, and now even
more hours can be whiled away, as the game has come to Android.
Steps to Run CS 1.6 on Android :
1) Install the APK from here: http://goo.gl/jq471I
Install APK with omp post fix if you have multi-core device and noomp
if you have single-core device.
2) Install the latest Xash3D Android from the below link
goo.gl/dBO9em
3) Copy cstrike and valve folders from your Steam CS1.6 installation
to xash folder on SD Card.
4) Run CS 1.6 Client!
How to Play Counter Strike 1.6 on Android
flashing a wrong file which led your phone to stuck at the boot logo
which is bootloop. Now you want to fix it yourself. So how will you
fix it ?
In this guide I will show you how to fix bricked/bootlooped phone
1. If Your Phone Keeps Rebooting: Wipe Your Data and Cache
2. If Your Phone Boots Straight Into Recovery: Flash a New ROM
3. If Your Phone Boots Straight Into its Bootloader: Restore From a Stock ROM
How to Fix Any Phone:
For Motorola Phones:
If you have a Motorola phone, you'll need to use RSD Lite, the program
that Motorola and its partnered carriers use to restore almost-bricked
phones.
For HTC Phones:
HTC phones can flash stock ROMs, known as RUUs, right from the phone's
bootloader. You'll need to Google around for your device's specific
RUU file, but once you download it, save the ZIP file to your SD card,
and rename it (to something like PG05IMG.zip—the download page for the
RUU file should specify which filename is required), booting up your
phone should automatically flash the stock ROM from HBOOT, HTC's
bootloader.
For Samsung Phones:
If you're using a Samsung Galaxy phone, you can use a tool called Odin
to reflash an OPS file, which is a stock ROM that will return your
phone to factory settings.
If You Get Errors with Any of The Above Methods: Reformat Your SD Card
and Don't Give Up
How to fix Bricked/Bootlooped Android Phones
And they are in a dilemma that whether to root their expensive Android
Phones
So here is a guide for advantages and disadvantages of rooting
Advantages :
1. Run Special Applications
After you have rooted your phone, you can run special applications
that require root access on your phone. When compared to regular
applications, root applications provide more features. As these
special apps can directly deal with the Android system files, they can
tweak your Android in more extensive ways.
2. Run Custom ROMs
One of the main reasons I rooted my phone was because I wanted
toinstall and use custom ROMs on it.These custom ROMs bring many teaks
and performance fixes and are much more user friendly when compared to
the stock ones. They are optimized in performance and battery
areupdated more frequently than the stock ROMs.
3. Free Internal Storage
People who have low internal memory can transfer any application from
internal memory to SD card after rooting their phone. There are some
applications that provide the option by default. But if you want to
force move an app by creating a symlink, you must use an app that only
works on a rooted phone.
So those were about the merits. Nothing's perfect and there are
certain caveats associated with rooting an Android device.
Disadvantages :
1. Your Phone Might Get Bricked
Not to demotivate you here, but when I tried to root my first Android
phone– Samsung Galaxy Y bricked it and it was in the service center
for next 15 to 20 days. No matter how good a rooting tutorial is, it's
a daunting task and if you miss out any step or flash a corrupt zip
file (that's what happened to me) you might end up with a bricked
(broken) phone.
2. You End up Voiding Phone's Warranty
As soon as you root your phone, you void your phone's warranty and if
anything happens to your phone even when it's in the warranty period,
the company is going to charge you for the repairs. In some of the
phones, you can un-root your phone, but in most of the phones there's
is no going back.
Conclusion :
So, you've been acquainted and warned. If you think that rooting the
phone to run special applications and custom ROM is worth is, go
ahead. If you think it's not worth the hassle, stay put. At the end of
the day, it's depends on your usage and what you want your phone to do
for you. Of course, proceeding with caution no matter how great an
expert you think you are is always advisable.
The bricking incident never stopped me from rooting my phone again.
Soon I will post a guide on how to fix any bricked phone keep visiting
Advantages and Disadvantages of Rooting Android
Rooting is the process of allowing users of smartphones tablets and
other devices running the Android mobile operating system to attain
privileged control(known as root access) over various Android
subsystems. As Android uses the Linux kernel, rooting an Android
device gives similar access to administrative ( superuser) permissions
as on Linux or any other Unix-like operating system such as FreeBSDor,
OS X
Why rooting is done :
Rooting is often performed with the goal of overcoming limitations
that carriersand hardware manufacturers put on some devices. Thus,
rooting gives the ability (or permission) to alter or replace system
applications and settings, run specialized applications("apps") that
require administrator-level permissions, or perform other operations
that are otherwise inaccessible to a normal Android user. On Android,
rooting can also facilitate the complete removal and replacement of
the device's operating system, usually with a more recent release of
its current operating system.
For how to root android devices see my previous post
Link : Click Here
What is rooting Android Devices
rooting an android phone and the risk of bricking their phones stops
them from rooting.
Note : You may lose your warranty after rooting
So here is a step by step guide to root your android device easily
with just one click
Note : It is a safe method to root android devices you don't need to
worry about it
Here we will be using an app called Kingroot
Download : www.apkmirror.com/wp-content/uploads/uploaded/55f75e1bcdcaf/com.kingroot.kinguser-4.5.0-120-minAPI8.apk
Download and install Kingroot from the above link.
Steps :
1. Tap on the KingRoot Icon to Open it.
2. Now, Tap on theStart Root Button to begin the root process.
3. Now Kingroot will start the rooting process
4. Within a minute or two you will be able to see the Big Green Tick,
which signifies that your device is rooted successfully.
5. Restart your Android Device. Voila you have sucessfully rooted your
android device
6. You can see a Kinguser app in your app drawer use it to manage root settings
Keep in mind :
Your Android Device should have atleast 20 percent of device battery
or more to begin the root process.
Advantages of using Kingroot for rooting :
[*] Powerful Tool: KingRoot is a very powerful tool, that allows you
to root Android Devices from android 2.3 to 5.1 without any issues.
[*] No data loss process:
Your Android Phone Data like contacts, pictures, videos, music and etc
will be not affected with this method.
Note : Your may lose your device warranty after rooting
How to root any Android Device with a tap
Some of the skills that hackers have are programming and computer networking skills. They often use these skills to gain access to systems. The objective of targeting an organization would be to steal sensitive data, disrupt business operations or physically damage computer controlled equipment.Trojans, viruses and worms can be used to achieve the above stated objectives.
In this article, we will introduce you to some of the ways that hackers can use Trojans, viruses and worms to compromise a computer system. We will also look at the counter measures that can be used to protect against such activities.
Topics covered in this tutorial
*.What is a Trojan?
*.What is a worm?
*.What is a virus?
*.Trojans, viruses and worms counter measures
What is a Trojan horse?
A Trojan horse is a program that allows the attack to control the user’s computer from a remote location. The program is usually disguised as something that is useful to the user. Once the user has installed the program, it has the ability to install malicious payloads, create backdoors, install other unwanted applications that can be used to compromise the user’s computer etc.
The list below shows some of the activities that the attacker can perform using a Trojan horse.
*.Use the user’s computer as part of the Botnet when performing distributed denial of service attacks.
*.Damage the user’s computer (crashing, blue screen of death etc.)
*.Stealing sensitive data such as stored passwords, credit card information etc.
*.Modifying files on the user’s computer
*.Electronic money theft by performing unauthorized money transfer transactions
*.Log all the keys that a user presses on the keyboard and sending the data to the attacker. This method is usedto harvest user ids, passwords and other sensitive data.
*.Viewing the users’screenshot
*.Downloading browsing history data
What is a worm?
A worm is a malicious computer program that replicates itself usually over a computer network.
An attacker may use a worm to accomplish the following tasks;
*.Install backdoors on the victim’s computers. The created backdoor may be used to create zombie computers that are used to send spam emails, perform distributed denial of service attacks etc. the backdoors can also be exploited by other malware.
*.Worms may also slow down the network by consuming the bandwidth as they replicate.
*.Install harmful payload codecarried within the worm.
What is virus?
*.A virus is acomputer program that attaches itself to legitimate programs and files without the user’s consent. Viruses can consume computer resources such as memory and CPU time. The attacked programs and files are said to be “infected”. A computer virus may be used to;
*.Access private data such as user id and passwords
*.Display annoying messages to the user
*.Corrupt data in your computer
*.Log the user’s keystrokes Computer viruses have been known to employ social engineering techniques. These techniques involve deceiving the users to open the files which appear to be normal files such as word or excel documents. Once the file is opened, the virus code is executed and does what it’s intended to do.
Trojans, viruses and worms counter measures
*.In order to protect against such attacks, an organizationcan use the following methods.
*.A policy that prohibits users to download unnecessary files from the internet such as spam email attachments, games, programs that claim to speed up downloads etc.
*.Anti-virus software must be installed on all user computers. The anti-virus software should be updated frequently and scans must beperformed at specified time intervals.
*.Scan external storage devices on an isolated machine especially those that originate from outside the organization.
*.Regular backups of critical data must be made and stored on preferably read only media such as CDs and DVDs.
*.Worms exploit vulnerabilities in the operating systems. Downloading operating system updates can help reduce the infection and replication of worms.
*.Worms can also be avoided by scanning all email attachments before downloading them.
Learn everything about Trojans, Viruses and Worms
Information plays a vital role inthe running of business, organizations, military operations etc.Information in the wrong hands can lead to loss of business or catastrophic results.
To secure communication, a business can use cryptology to cipher information. Cryptology involves transforming information into non human readable format and vice versa.
In this article, we will introduce you to the world of cryptology and how you can secure information from falling into the wrong hands.
Topics covered in this tutorial
*.What is cryptography?
*.What is cryptanalysis?
*.What is cryptology?
*.Encryption Algorithms
Now!What is Cryptography?
Cryptography is the study and application of techniques that hide the real meaning of information by transforming it into non human readable formats and vice versa.Let’s illustrate this with the aid of an example. Suppose you want to send the message “I LOVE APPLES”, you can replace every letter in the phrase with the third successive letter in the alphabet. The encrypted message will be “K NQYG CRRNGV”. To decrypt our message, we will have to go back three letters in the alphabet using the letter that we want to decrypt. The process of transforming information into non human readable form is called encryption.The process of reversing encryption is called decryption.Decryption is done using a secret key which is only known to the legitimate recipients of the information. The key is used to decrypt the hidden messages. This makes the communication secure because even if the attacker manages to get the information, it would not make sense to them.The encrypted information is known as a cipher.
What is Cryptanalysis?
Cryptology encrypts messages using a secret key.Cryptanalysis is the art of trying to decrypt the encrypted messages without the use of the key that was used to encrypt the messages. Cryptanalysis uses mathematical analysis & algorithms to decipher the ciphers. The success of cryptanalysis attacks depends on;
*.Amount of time available
*.Computing power available
*.Storage capacity available
The following is a list of the commonly used Cryptanalysis attacks;
*.Brute force attack– this type of attack uses algorithms that try to guess all the possible logical combinations of the plain text which are then ciphered and compared against the original cipher.
*.Dictionary attack– this type of attack uses a wordlist in order to find a match of either the plain text or key. It is mostly used when trying to crack encrypted passwords.
*.Rainbow table attack– this type of attack compares the cipher text against pre-computed hashes to find matches.
What is crypotology?
Cryptology combines the techniques of cryptography and cryptanalysis.
Encryption Algorithms MD5– this is the acronym for Message-Digest 5. It is used to create 128 bit hash values. Theoretically, hashes cannot be reversed into the original plain text. MD5 is used to encrypt passwords as well as check data integrity. MD5 is not collision resistant. Collision resistance is the difficulties in finding two values that produce the same hash values.
*.SHA– this is the acronym for Secure Hash Algorithm. SHA algorithms are used to generate condensed representations of a message (message digest). It has various versions such as;
*.SHA-0: produces 120 bit hash values. It was withdrawn from use due to significant flaws and replaced by SHA-1.
*.SHA-1: produces 160 bit hash values. It is similar to earlier versions of MD5. It has cryptographic weakness and is not recommended for use since the year 2010.
*.SHA-2: it has two hash functions namely SHA-256 and SHA-512. SHA-256 uses 32 bit words while SHA-512 uses 64 bit words.
*.SHA-3: this algorithm was formally known as Keccak.
*.RC4– this algorithm is used to create stream ciphers. It is mostly used in protocols such as Secure Socket Layer (SSL)to encrypt internet communication and Wired Equivalent Privacy (WEP)to secure wireless networks.
*.BLOWFISH– this algorithm is used to create keyed, symmetric blocked ciphers. It can be used to encrypt passwords and other data.
How to make your data safe using Cryptography
Learn everything about ethical hacking tools and skills
Skills allow you to achieve your desired goals within the available time and resources. As a hacker, you will need to develop skills that will help youget the job done. These skills include learning how to program, use the internet, goodat solving problems, and takingadvantage of existing security tools.
In this article, we will introduce you to the common programming languages and skills that you must know as a hacker.We will also look at tools that you can use to identify and exploit security weaknesses in computer systems.
Topics covered in this tutorial
*.What is a programming language?
*.Why you should learn how to program?
*.Other Skills
What is a programming language?A programming language is a language that is used to develop computer programs. The programs developed can range from operating systems;data based applications through to networking solutions.
Why you should learn how to program?
*.Hackers are problem solver and tool builders, learning how to program will help you implement solutions to problems. It also differentiates you from script kiddies.
*.Writing programs as a hacker, will help you to automat many taskswhich would usually take lots of time to complete.
*.Writing programs can also help you identify and exploit programming errors in applicationsthat you will be targeting.
*.You don’t have to reinvent thewheel all the time, there are a number of open source programs that are readily usable.
You can customize the already existing applications and adding your own methods to suit your needs.
What languages should I learn?
The answer to this questiondepends on your target computer systems and platforms. Some programminglanguages are used to develop for only specific platforms. As an example, Visual Basic Classic (3, 4, 5, and 6.0) is used to write applications that run on windows operating system. It would therefore be illogical for you to learn how to program in Visual Basic 6.0 when your target is hacking Linux based systems.
Other skills
In addition to programming skills, a good hacker should also have the following skills:
*.Know how to use the internet and search engines effectivelyto gather information.
*.Get aLinux based operating systemand the know the basics commands that every Linux user should know.
*.Practicemakes perfect, a good hacker should be hard working andpositively contribute to the hacker community. He/she can contribute by developing open source programs, answering questions in hacking forums etc.